New Security Reality - An AI Defense for Weaponized AI
Truth is ancient though it seems an upstart.
-Elizabethan Master George Silver, Gentleman
George Silver, author of the "Paradoxes of Defence" in 1599, was one of the last, classical Masters of London, what we would think of today as the quintessential knight in shining armor. He wrote Paradoxes because technology was shifting and with it, he saw everyone collectively lose their minds and throw out everything they knew.
And, yes, OK, he was also a little cranky about the technology change itself - specifically the Italian rapier which was accompanied with a fighting style that, applied correctly, spread far slower than the weapon itself.

Illustration from "Paradoxes of Defence", George Silver, 1599
Seriously, it takes about 5 minutes. That's because online attacks were the first to fully embrace automation. Automation is the first stage of maturity when it comes to machine learning and AI, but the next wave already in use in some dark corners of the web have brought something far more dangerous.
The four grounds or principals of that true fight at all manner of weapons are these four:
- Judgment
- Distance
- Time
- Place
-George Silver
Silver broke down defense for us into four universal truths followed by a long list of specific strategies related to the tools used. Let's take a look at how to apply some of that ancient knowledge to some specific instruments of today. Every strategy should be different, so we're going to pick on a common, modern architecture, list some of the typical threats, and lay out a plan of defense that adds some practical AI. Your situation is almost certainly different and nuanced, but hopefully this example's use of Judgment, Distance, Time, and Place is a good starting point to guide your solutions.
What You Expected to Happen
Our example is going to use a set of microservices, run in containers for better isolation, over HTTPS for encrypted communication, and a firewall configured properly to prevent anything but expected API use from passing through. A great start! The ops are solid. What could go wrong?
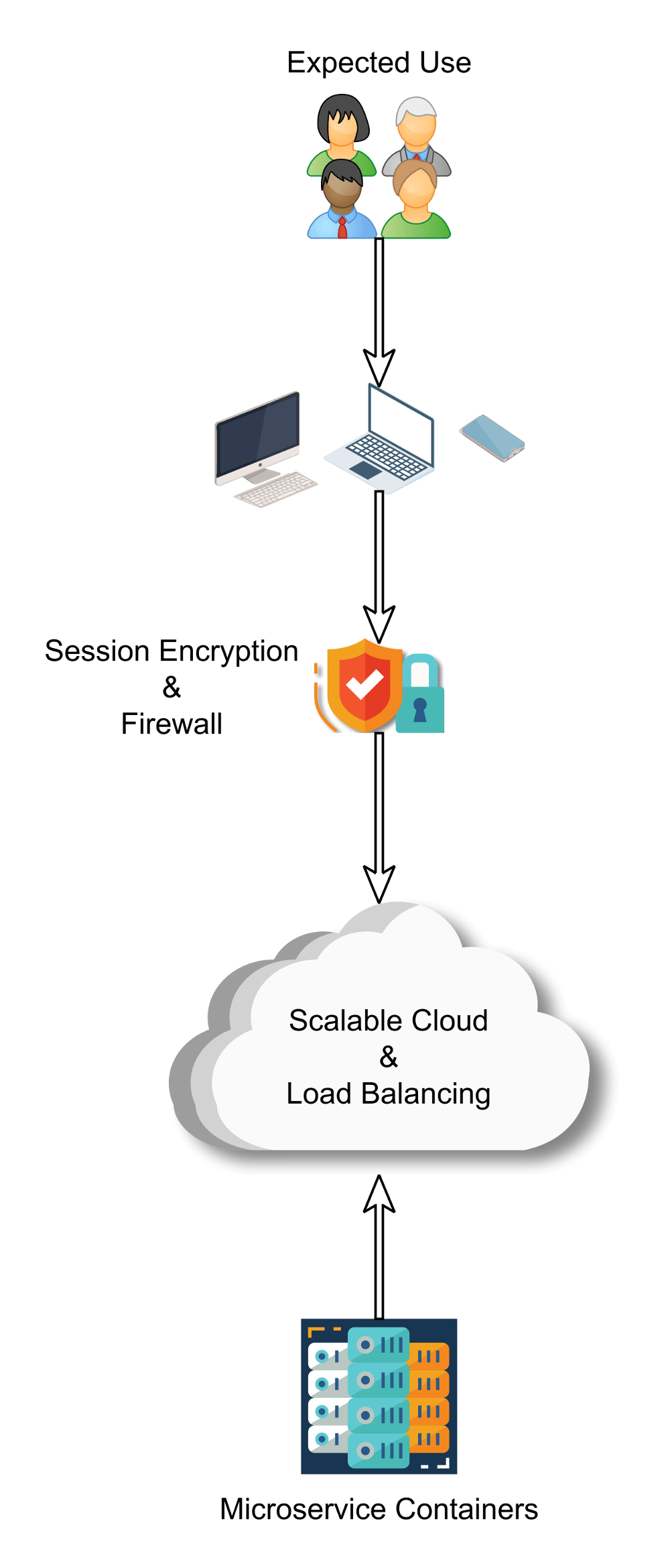
What Happens Instead
Probably before your first legitimate user logs in you'll start seeing your logs filling up with bots. You blocked regions that you don't expect users to be coming from with your firewall? That's nice, not every app has that luxury, but compromised systems and IoT devices cover every region. The more sophisticated ones are working together, have updated known exploit lists, and can alert people with destructive tendencies when they find an issue.
Your systems, designed to be helpful to developers and legitimate users, are equally helpful to attackers. Even wild, random attempts probably provide good intel on what kinds of services are running, what versions they're running, and more. This can escalate into increasingly targeted attacks.
Oh, and your end users are also on the receiving end of same style of attacks, so don't expect you can trust that all of their requests are actually from them.
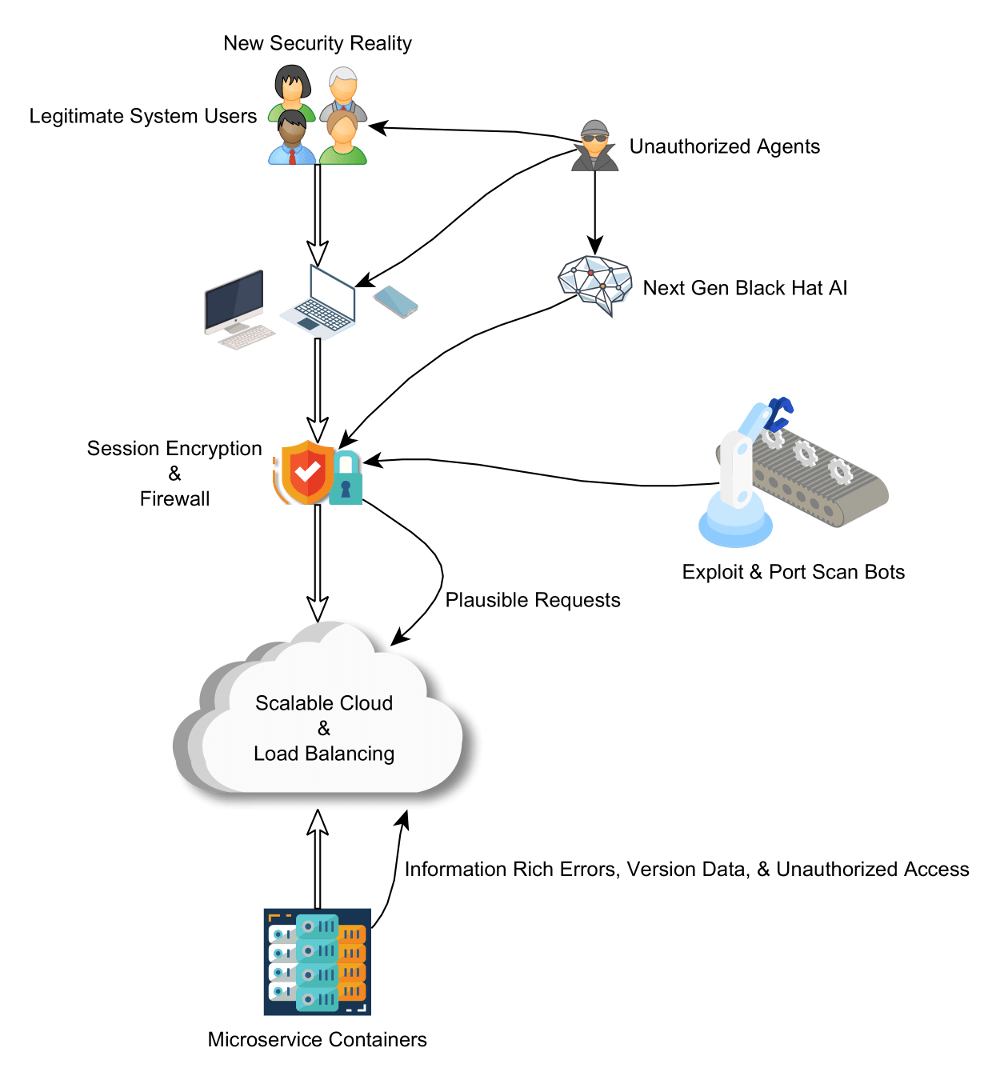
But while there may be some basic algorithms and lookup tables for the bots, by and large they rely upon wide spread and fairly well known bugs. Enter AI. Deeply personalized - individualized even. Learning and working over long running workflows but at incredible speeds. Connecting the dots across multiple sources of information to look for unexpected correlations and make predictions. There's a reason the world is getting excited for Industry 4.0! Unfortunately, each of these represent a double edged sword.
What if you have an exploit that only exists for you, via the exponential combinations of some random sets of configurations, via the software or software integrations you use, or through APIs that are supposed to trust authorized users even if they're compromised? That's where AI and especially human assisted AI becomes weaponized, finding ever more creative ways in.
The Four Grounds of Defense, AI Edition
Before we begin formulating a defense, a word of warning as one last story from Gentleman Silver.
There was a cunning Doctor at his first going to sea, being doubtful that he should be sea sick, an old woman perceiving the same, said unto him: "Sir, I pray, be of good comfort, I will teach you a trick to avoid that doubt. Here is a fine pebble stone, if you please to accept it, take it with you, and when you are on ship board, put it in your mouth, and as long you shall keep the same in your mouth, upon my credit you shall never vomit." The Doctor believed her, and took it thankfully at her hands, and when he was at sea, he began to be sick, whereupon he presently put the stone in his mouth, & there kept it so long as he possibly could, but through his extreme sickness the stone with vomit was cast out of his mouth. Then presently he remembered how the woman had mocked him, and yet her words were true.
-George Silver
Beware of magical thinking and, to pardon the pun, Silver bullets. Security is incredibly hard because it is thinking about what isn't or shouldn't be there, not how it should be. Advanced AI systems are also hard, and any technology advanced enough lures humanity into the magical thinking fallacy.
That doesn't mean we should give up, but it does mean that you should invest in thoughtful security strategies in proportion to the risk of a breach.
OK, let's get to the diagram. It's getting a little crowded so, first let me show you just what's new:
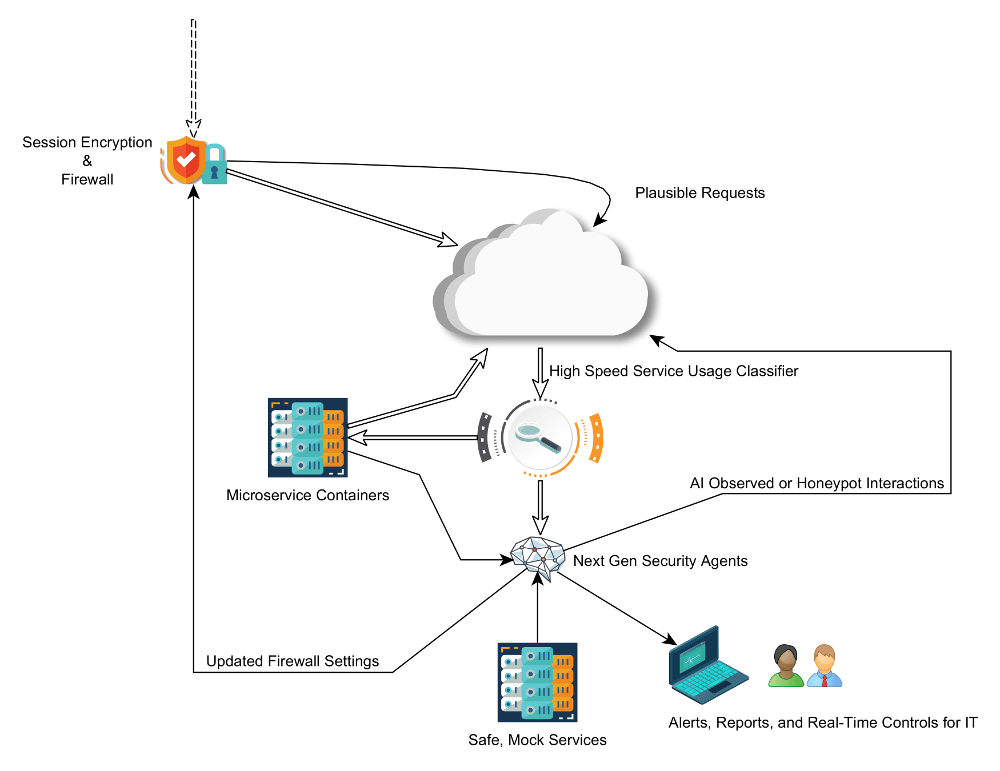
Judgment & Measure
By pre-training a high speed model designed to recognize legitimate traffic from potential threats, you can keep an unblinking eye on service traffic at the load balancing layer, behind fully encrypted traffic but still blind to confidential field level encryption of things like personally identifiable information (PII). The job of the classifier is to measure the signature of communications and place a threat score on it, including dimensions of time and coordination of multiple requests.
It does not log, it only scores at a rapid pace and events that reach a high enough threat level are then passed on for further evaluation. Like a fencer circling and watching for signs of attack with the intuition of experience, the classifier is continuously taught by real events in a side process that doesn't bottleneck your high performance services.
Legitimate volume spiking and you need to start letting traffic through without it all being seen? Begin randomly picking messages instead so that you don't totally lower your defenses.
Time & Place
Once the ML model has found something of interest, that's when you power up a dedicated AI service to do the heavy lifting. Next generation AI security agents are designed to learn new attack vectors as they come in, deal with them, and update the more static services to watch out for them in the future. They also report back to your security team so that potential vulnerabilities can be patched. In the case of ongoing, active attacks, additional tools can be made available for real-time responses - AI empowered humans taking the wheel.
OK, you're under a new form of attack. Sure, you need to stop it, but you also need to learn from it. Isolate the attack, picking your own higher ground, so you can safely take your time to learn. For example, your defensive AI can trigger a "honeypot" environment that tricks the attacker into thinking they're talking to your real services but instead their every move is being studied against a false, mock server.
Here's what it looks like altogether, with a much more balanced approach to security.
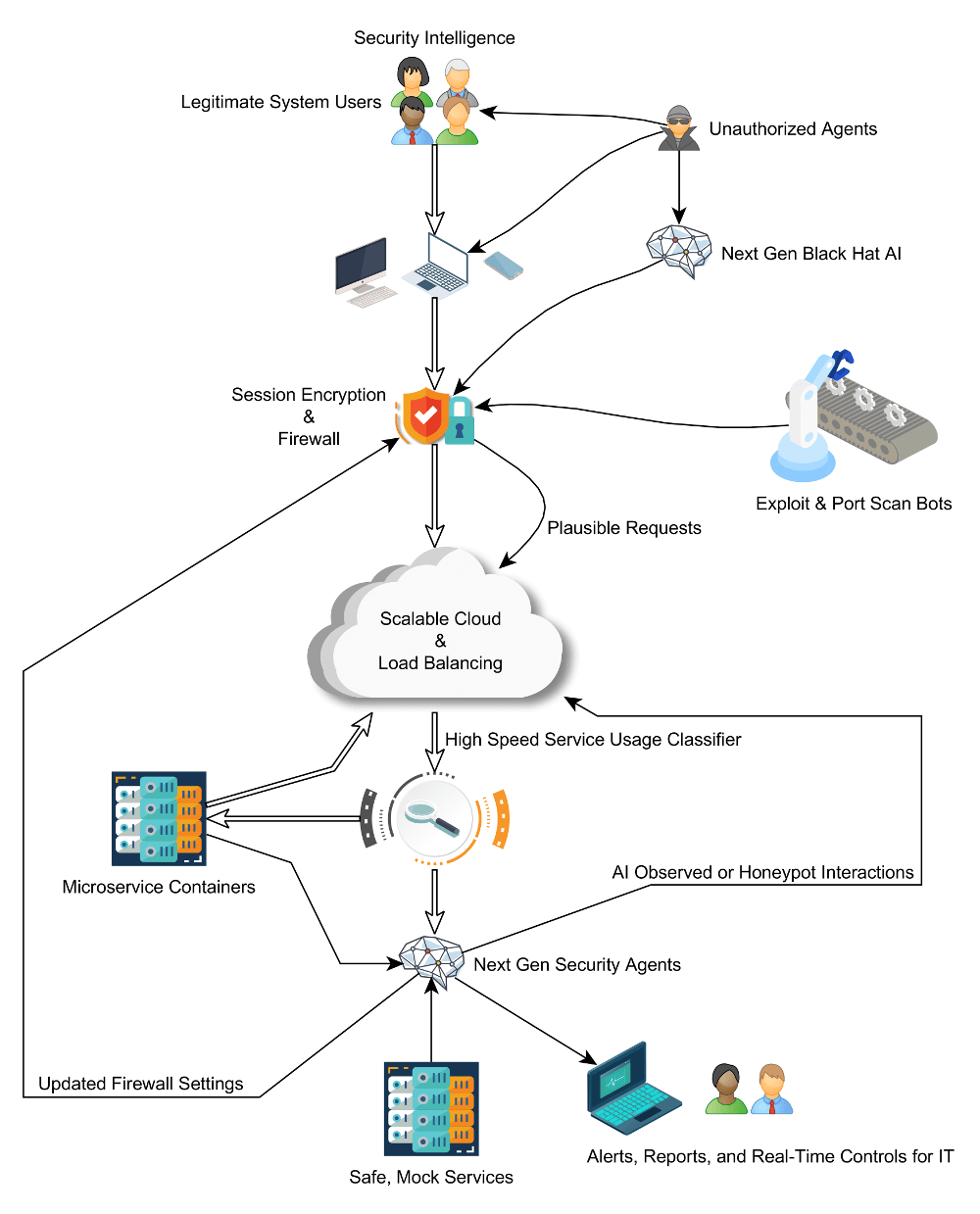
As the tools continue to evolve, so will the strategies, but the fundamentals will remain the same. Embrace new tools without forgetting the timeless lessons of security, and risk can be managed in this new arms race. In doing so you not only protect your systems, but your customers and employees. There's much more to be said, but for now, let's all adapt and learn together to face fresh challenges.
Subscribe to Tinman Kinetics
Get the latest posts delivered right to your inbox
